
 “LanScope Cat” is an all-in-one package comprising the necessary functions for information leak countermeasures and IT asset management. With the ability to choose only the necessary functions, LanScope Cat is a security tool that solves the problems many business face concerning IT asset management and information security and supports business success.
“LanScope Cat” is an all-in-one package comprising the necessary functions for information leak countermeasures and IT asset management. With the ability to choose only the necessary functions, LanScope Cat is a security tool that solves the problems many business face concerning IT asset management and information security and supports business success.
By implementing our CAT system (Check, Action, Trace), we build the systems you need to manage your important assets, perform information security measures and stop leaks in their tracks.

Check
We learn what type of computers you have on your network,and how those computers are used.

Action
By implementing the appropriate measures against risk,it is possible to prevent major problems from occurring.

Trace
In the worst case scenario,we go back over past data and trace the cause of the problem.
Advantages
- Update hardware and software information everyday to maintain an accurate environment without hassle of management tasks.
- By managing PC operations logs, it is possible to improve security and find problems in emergencies, without reducing operational efficiency.
- Monitor web site use, and limit access to illicit sites.
- Control use of devices such as USBs and CDs, and prevent the leaking of important secret information.
- LanScope Cat Protection includes CylancePROTECTR, an endpoint malware prevention product powered by artificial intelligence and machine learning.
Features Overview
Asset Management

Hardware Management
 Automatically collect over 50 types of hardware information, such as computer name and IP address, as well as optionally set registry data. Optionally record and manage printers and other peripheral devices. Also, it is possible to check necessary information by searching with a variety of conditions.
Automatically collect over 50 types of hardware information, such as computer name and IP address, as well as optionally set registry data. Optionally record and manage printers and other peripheral devices. Also, it is possible to check necessary information by searching with a variety of conditions.
Software Management
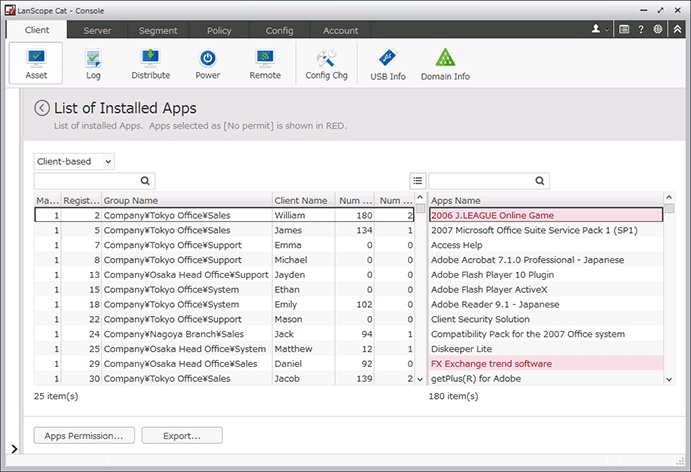 Check program updates, messages and questionnaires, and whether program updates are installed on PCs. Classify permitted and forbidden apps and manage information such as how many machines each app is installed on and their product keys.
Check program updates, messages and questionnaires, and whether program updates are installed on PCs. Classify permitted and forbidden apps and manage information such as how many machines each app is installed on and their product keys.
Operation Log Management
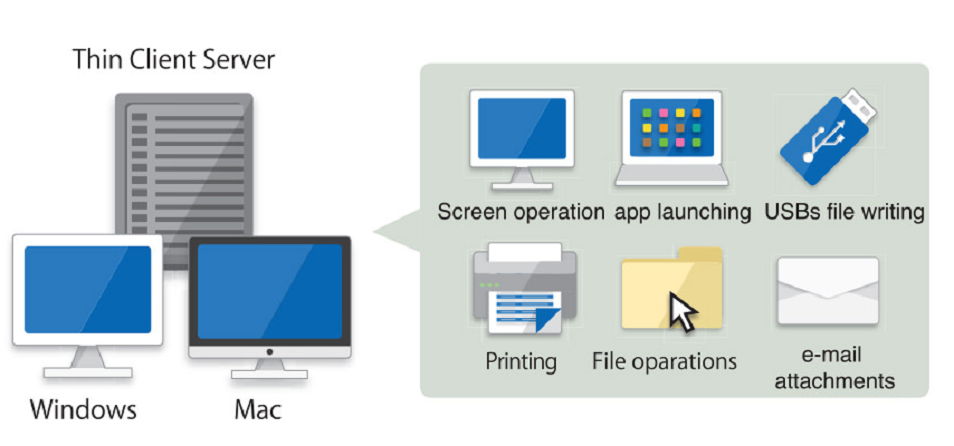
Operation Log Management
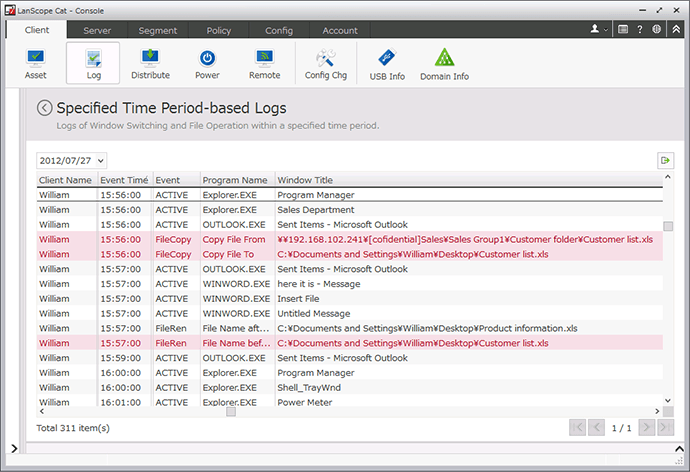
Record "who" did "what" "when" at "which PC". If some operational violation that could be an information leak occurs, such as writing a customer list to a USB, a warning is displayed to the user, and the illicit operation is prevented.
Print Log Management
Record "who" printed "how many pages" of "what" "when" at "which PC". Discover wasteful printing and reduce costs. If particular files are printed, a warning is displayed to the user and illicit printing is prevented.
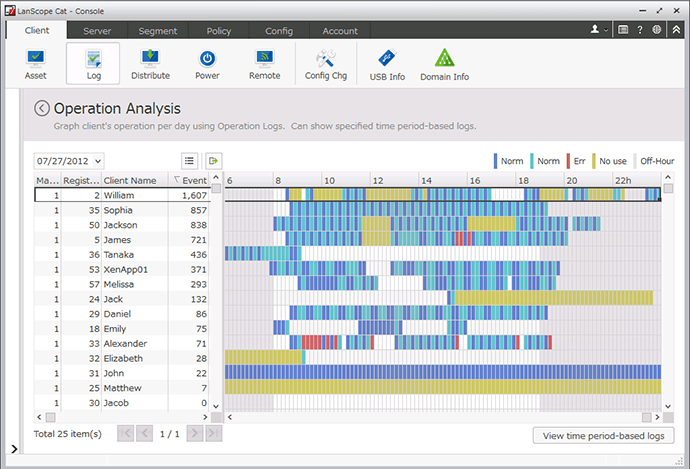
Operation Analysis
See the status of PCs in a color-coded graph.
App Usage Management
Record "who" used "which app" "when" at "which PC". See how many instances of each app are running on PCs and for how long. Reduce wasteful license costs by allotting the ideal number of licenses.
App Prohibition
Prohibit launching illicit apps or apps unrelated to work. If a particular app is launched, a warning is displayed to the user and apps such as games or those that can result in information leaks are suppressed.
Web Access Management

Web Access Management
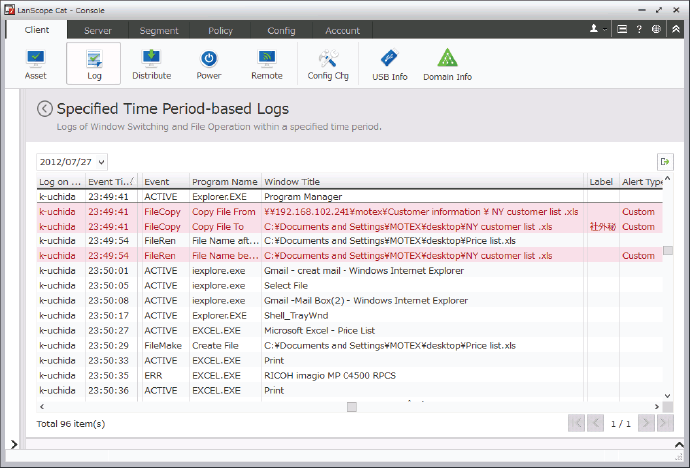 Record "who" views "which web site" "when" on "which computer". If an illicit web site is viewed, it is possible to display an alarm or block access. Also, it is possible to limit uploads and downloads and record what information is posted to the web in Internet Explorer.
Record "who" views "which web site" "when" on "which computer". If an illicit web site is viewed, it is possible to display an alarm or block access. Also, it is possible to limit uploads and downloads and record what information is posted to the web in Internet Explorer.
White List
 Designate keywords to only allow access to specific web sites.Create an environment where only web sites necessary for work, such as groupware and cloud services, can be accessed.
Designate keywords to only allow access to specific web sites.Create an environment where only web sites necessary for work, such as groupware and cloud services, can be accessed.
Device Control
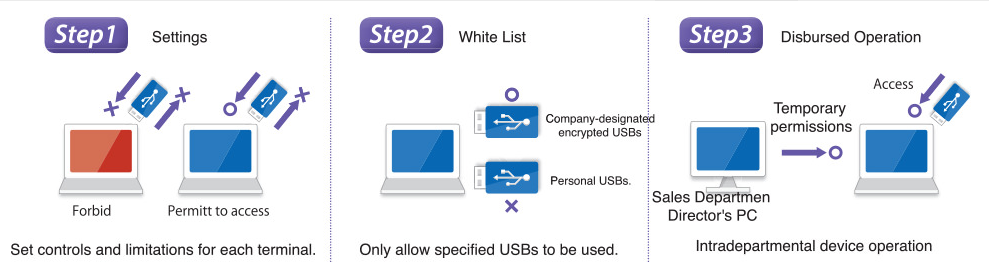
Device Control
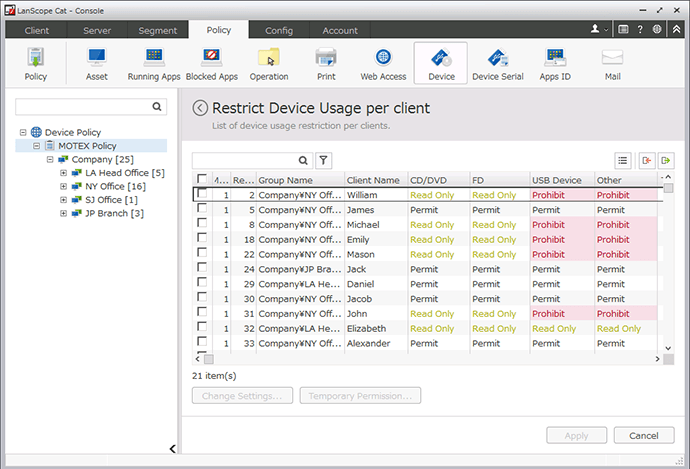 Manage all company devices and limit their use. If a prohibited device is connected, the user is notified that it is prohibited and illicit use is controlled. Also, allow device use in limited situations through setting detailed conditions by PC and device to adapt to the workplace.
Manage all company devices and limit their use. If a prohibited device is connected, the user is notified that it is prohibited and illicit use is controlled. Also, allow device use in limited situations through setting detailed conditions by PC and device to adapt to the workplace.
Set usage limits for each terminal
Control or forbid the use of CDs, DVDs, USBs, etc. by type. Also, flexible settings allow each PC to be set to disable reading and writing, disable only writing, etc.
Set USB permissions
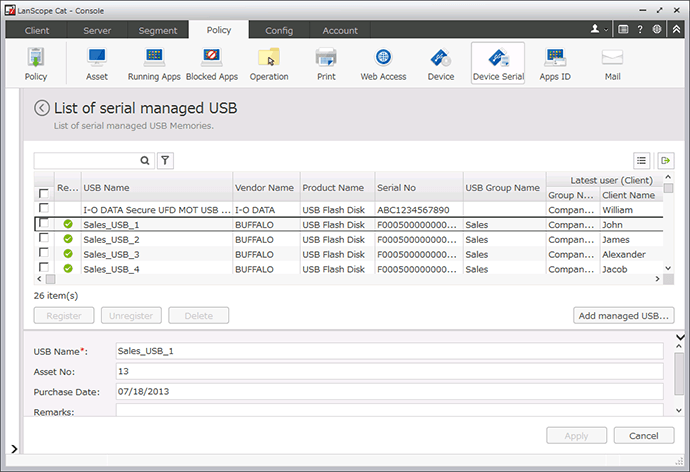 Designate device names (nicknames), manufacturer numbers (serial numbers), or only allow company-issued devices and forbid the use and connection of other devices.
Designate device names (nicknames), manufacturer numbers (serial numbers), or only allow company-issued devices and forbid the use and connection of other devices.
System Environment
Server
| OS | Windows Server 2008 (32bit/ 64bit)/ 2008 R2/ 2012/ 2012 R2/ 2016 |
| CPU | 2.0 GHz |
| Memory | 4 GB or more |
| HDD free space | 200 GB or more |
| Database | SQL Server 2008/ 2008 R2/ 2012/ 2014 |
| Web Console Browser | Internet Explorer 10/ 11/ Google Chrome Ver.43.0.2357/ Mozilla Firefox Ver.38.0.5 |
Client
| OS | Windows XP/ Vista/ 7/ 8/ 8.1/ 10 Windows Server 2003/ 2003 R2/ 2008/ 2008 R2/ 2012/ 2012 R2/ 2016 |
| CPU | 300 MHz or more |
| Memory | 128 MB or more |
| HDD free space | 50 MB or more |
For more information, visit www.lanscope.jp/cat/en/